INFRASTRUCTURE AND SECURITY
Infrastructure and Security
The foundations of our platform and its services
At Jotelulu, we take security very seriously.
We are aware of the importance of security for our customers. That is why we work constantly to provide the most secure infrastructure, platform and services. We work to continuously improve in different areas to maintain and improve our quality and security standards.

At Jotelulu, we host our platform and infrastructure in advanced data centres that we have chosen based on strict security, quality, efficiency and connectivity criteria.
We host our services in different data centres in Europe, partnering with industry leaders such as Digital Realty (formerly Interxion) and Equinix. They are considered top-tier data centres and are probably among the most advanced built to date. In addition, they are neutral-network data centres and have a broad range of connectivity which allows us to offer greater redundancy and connection availability.
Furthermore, our data centres have strict security measures relating to physical access, environmental conditions and power, guaranteeing maximum service quality.
PHYSICAL SECURITY MEASURES
Access to our data centres is controlled by security personnel 24/7. They are monitored by CCTV and can only be accessed with prior authorisation.
Security Measures:
- 24-hour security guards.
- 24/7 continuous recording.
- Metal detector and turnstiles to access the data centre.
- Cameras on access doors and corridors (external and internal).
- 5 layers of physical security (access to the perimeter, building, technical rooms, rack wardrobes, etc.)
ENVIRONMENTAL CONTROLS
Our IT equipment is maintained and monitored in controlled environments with SLAs relating to temperature and humidity:
- Continued refrigeration (24h).
- Redundant air conditioning equipment.
- 21°C temperature and relative humidity of 50%.
Similarly, all servers are protected against fire through a sprinkler system designed to extinguish any fire in seconds and without leaving residue:
- Smoke detectors
- Automatic extinguishing systems
- Manual emergency stop buttons in all rooms.
- Optical and ionic sensors with VESDA system
- 24/7 monitored alarm system.
POWER SUPPLY
The data centres where Jotelulu hosts its infrastructure are equipped with redundant power supply connections and appropriately sized kinetic diesel generators to support the energy needs of the entire building and all the infrastructure hosted inside it.
DATA CENTRES CERTIFICATED BY INTERNATIONAL STANDARDS:

At Jotelulu, we have implemented 100% redundant architecture to ensure that the failure of any system element will not impact the operation of our platform and its services.
COMPUTE NODES
Each host has a double power supply, each one connected to a different electrical part of the data centre. All equipment that makes up the infrastructure has at least two high-availability network connections (LAG). Similarly, each network connection goes to a different switch so that a switch failure will not result in a drop in service. The RAM memory used by our hosts is ECC, which protects us against data corruption and potential failures.
We also have Hypervisors on N x 1.25, so that we have enough space to support even a failure of 25%. If a hypervisor fails, the servers hosted in it will automatically boot on other hypervisors.
STORAGE
Jotelulu offers high-availability storage that combines clustering based on cabinets with synchronous mirroring to provide a transparent recovery from failures.
With this redundant storage system we achieve:
- Better protection against hardware, network or installation failures.
- Eliminate inactivity times and change management times.
- Update hardware and software without interrupting operations.
DATA NETWORK
We have various 10G circuits with different network providers for the data centre so that a problem with one provider will never affect connectivity.

The skeleton of the network within the data centre is made up of multi-chassis link aggregation. These links provide redundancy and scalability at the same time as preventing loops.
Each data centre has a pair of frontera routers that enable connection with the internet and other centres. After this, there are layer-3 aggregation switches, then layer-2 and then, lastly, access switches that the compute nodes connect to.
All logic switches are formed in pairs for redundancy and all devices are connected via multi-chassis link aggregation composed of two or more 10G or 40G connections. This avoids the risk of the formation of loops in layer 2.

Jotelulu’s infrastructure features Anti-DDoS systems to prevent and filter denial-of-service attacks, keeping our servers always available.
The structure of our Anti-DDoS system consists of various layers of filtering and detection which allow us to screen and separate small attacks (from a few hundred Mbps) from larger attacks of thousands of Gbps.
IDS/IPS
Our Intrusion Detection System (IDS) allows us to detect unauthorised access to our infrastructure. It acts by assessing an intrusion when it takes place and generates an alarm. The IDS is accompanied by an attack prevention tool, known as IPS, that continuously and proactively traces suspicious or unusual network traffic.
The IDS/IPS cannot stop attacks on its own and needs additional tools, such as Firewalls, to help block intrusions.
FILTERING AND BLOCKING ON PERIMETER FIREWALLS
Our perimeter firewalls continuously analyse the traffic that reaches our data centres and blocks clearly malicious traffic so that it does not reach the data centre. They also review the volume of traffic to each machine in order to detect potential DDoS attacks.

To ensure the greatest availability, at Jotelulu, we only use Solid State Disks (SSD and NVMes) from the top range (NetApp all-flash Cabinets).
Using this type of Enterprise disk aims to ensure:
THE BEST, MOST CONSISTENT PERFORMANCE
By using NetApp all-flash cabinets, we aim to ensure consistently excellent performance, regardless of the workload that the disk is subjected to or the level of usage.
DATA PROTECTION
The NetApp all-flash system provides an extra layer of protection to data in an integrated way. Synchronous replication, embedded encryption, WORM protection and multi-factor authentication are just some of the advantages that our storage cabinets have that help us to keep essential data available, protected and secure.

When accessing and handling data, security is something that we take very seriously at Jotelulu. That is why we have implemented a powerful data-encryption system and 2-factor authentication processes.
2-FACTOR AUTHENTICATION
2-factor authentication is an access control measure whereby the user is provided access to the system only once they have presented two different proofs that they are who they say they are.
At Jotelulu, we have made access to the platform and the portal more secure by implementing 2-factor Authentication (2FA) through an access token generated on a mobile device. The generated token for this software is a six-digit number that the user needs to provide as well as their username and password to access Jotelulu’s services.
ENCRYPTED DATA
Encryption is a data encoding process that converts original data (plain text) into an alternative form known as encrypted text that only authorised parties can decode. Any person who does not have the correct keys will not be able to read the information.
Jotelulu services use different encryption systems when handling and transferring data to give an extra layer of protection against potential hacks.

Jotelulu has a 24/7 monitoring and alerts system that makes it possible to keep an eye on the system status at all times, both the main infrastructure and subsystems. This way, we can assure the reliability and stability of our platform and its services.
Our 24/7 monitoring system consists of a combination of metrics and graphs with the establishment of various rules and alerts. The ultimate goal is to be fully up to date and alert to potential problems to prevent any downtime.

A backup is a copy of original data that is created in order to have a way of recovering the data if it is lost. Security copies are extremely useful in many different scenarios, and at Jotelulu, we have various backup policies for each of our services.
BACKUP POLICY FOR OUR REMOTE DESKTOP AND SERVERS SERVICES
The backup policy for our Remote Desktop and Servers services is based on snapshots (NetApp) in accordance with the following schedules:
- Every hour [previous 5 hours]
- Every day [previous 14 days at 00:10]
- Every week [previous 8 weeks – Sundays at 00:15]
BACKUP POLICY FOR OUR FILE STORAGE SERVICE
The File Storage service has a pre-set backup policy for all users to create granular, encrypted backups.
The security copies policy is detailed below:
Backup Frequency: 1 copy daily
Retention of Backups:
- Every hour [previous 5 hours]
- Every day [previous 14 days at 00:10]
- Every week [previous 8 weeks – Sundays at 00:15]
Furthermore, we use VSS volume snapshots that make it possible to restore previous versions of files and folders.
Scheduling of snapshots: Every day [12:00 and 18:00]
Retention of snapshots:
- 64 snapshots.
Instantaneous and online data recovery system available for any user.
REPLICAS OF S3 BUCKETS
The object storage system replicates each object on 3 different disks located on 3 different servers. The established policy will keep one of the copies on a different data centre by default.
The S3 Buckets service also has a versioning function that can be activated through the subscription settings on the platform at any time. This way, it is possible to recover previous versions through the S3 protocol.

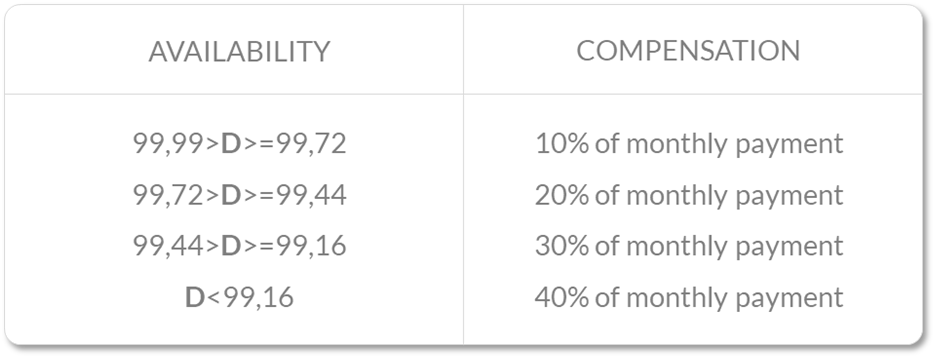
The following are not considered when calculating system availability:
- Causes outside of JOTELULU’s control or the result of force majeur.
- Unavailability of the self-management panel.
- Unavailability as a result of the failure of software hosted on virtual machines.
- Viruses and IT attacks that may cause the total or partial loss of access to services.
Support service availability:
The platform has a support/engineering team dedicated to maintenance, renovation and resolving incidents available at the following times:
- Critical incidents on the platform: 24/7 coverage.
- All other incidents or requests: Monday to Friday from 08:30 a 20:00 [UTC/GMT +1].
- Critical incidents: Response within 1 hour.
- Other incidents: Response within 4 hours.
- Inquiries: Response time within 24 hours.




