Today, we’re going to look at the steps to follow when carrying out a risk and threat assessment for an SME.
When it comes to defining a business’s security infrastructure or disaster recovery plan, one of the hardest steps is correctly identifying, evaluating and prioritising the relevant risks or threats.
A brief introduction to risk and threat assessment for SMEs
Risk assessment is a fundamental component of security planning in any company. This activity aims to identify and address any potential threats that could impact the company’s operations or even put its survival at risk.
To help you with this task, we’ve come up with a simple 9-step guide for you to follow and ensure that you’re fully prepared for anything that might arise.
- Step 1: Identify your company’s assets
- Step 2: Identify the potential threats
- Step 3: Evaluate any vulnerabilities
- Step 4: Estimate the potential impact
- Step 5: Estimate the probability of occurrence
- Step 6: Rank the potential risks
- Step 7: Implement mitigation strategies
- Step 8: Implement control measures
- Step 9: Continuous Improvement
So, let’s now take a look at each of them in more detail.
Step 1: Identify your company’s assets
You might remember, years ago, there was a tyre advert that carried the slogan “Power without control is nothing”. Personally, I think it’s one of the best marketing campaigns ever. You might also be familiar with the following quote by Lord Kelvin: “What is not defined cannot be measured. What is not measured, cannot be improved. What is not improved, is always degraded”.
Whether you’re familiar with these maxims or not, they form the foundations of what we’re about to talk about. The very first step to risk and threat assessment is to identify your company’s assets, making sure that you capture all of your most critical assets which could impact production or the company’s finances.
But, what is an asset? To answer this we’ll refer to the ITIL (Information Technology Infrastructure Library), which defines an asset as any financially valuable component that can contribute to the delivery of an IT product or service. So, anything from a server to a chair.
Now that you know what an asset is, it’s time to number and categorise each element of the business, including your IT systems, devices, physical facilities, data and even human resources.
You should also include any confidential information, customer data, intellectual property and other information that is critical to the running of your business.
Step 2: Identify the potential threats
Once you have identified your assets, it’s time to identify the potential threats that could affect them.
During this step, it’s not uncommon for you to stumble across other assets that you missed in Step 1. This is one of the reasons why we have Step 9, which seeks to continually review what you have done and check whether it needs updating.
Potential threats can include both physical threats and cyber threats. Physical threats are things like natural disasters, such as earthquakes, flooding, fires, etc. Cyber threats include things like viruses, malware, phishing, data exfiltration, backup failures, etc. And of course, we can’t forget other risks such as theft, a terrorist attack, an accident, sabotage or human error. You basically want to cover any possible event that has the potential to impact operations.
NOTE: Remember threats can be both internal and external.
As a reference, you might refer to the Magerit guides made available by the Spanish government, particularly the Threats section of the book on Techniques.
Step 3: Evaluate any vulnerabilities
Now that you’ve identified your assets and the potential threats that could affect them, it’s time to thoroughly examine your company’s vulnerabilities. To do this, you’ll need to review each system, process and security control and identify every possible point that could be exploited by an attacker.
You will need to consider all potential security breaches, whether they concern network components, protocols, operating systems or something else. Especially review software components, such as applications or services, bearing in mind that a lack of updates or obsolescence can make these susceptible to failure or attack.
NOTE: It’s good practice to keep your apps and systems updated and check the latest attack reports, security trends or zero-day attacks.
Step 4: Estimate the potential impact
Once you’ve identified your assets, the potential threats and your company’s vulnerabilities, it’s time to think about the potential impact of each threat. To do this, you should go through each asset, threat or vulnerability, one by one, and think carefully about:
- The financial impact or cost.
- The operational disruption to the business.
- How much data would be lost
- Potential reputational damage
- And, above all, the human impact
Step 5: Estimate the probability of occurrence
Now it’s time to consider how likely each threat is to occur. To do this, you should refer to trend data, previous risk assessments, historical data and any other experiences that might provide you with some insight.
Step 6: Rank the potential risks
OK. So far, you have identified your critical assets, potential threats and where the weak points are in your business. You’ve also rated the severity of the impact and the likelihood of each threat occurring.
Now it’s time to use this information to rate the level of risk associated with each threat. To do this, we just use the following formula:
RISK = PROBABILITY x IMPACT
By describing risk in this way, we will be able to allocate the necessary resources to the most urgent or critical threats.
While we have used categories for this exercise (High Probability, High Impact, etc.), many companies choose to use a scale of 1-10. Choose whichever you’re most comfortable with.
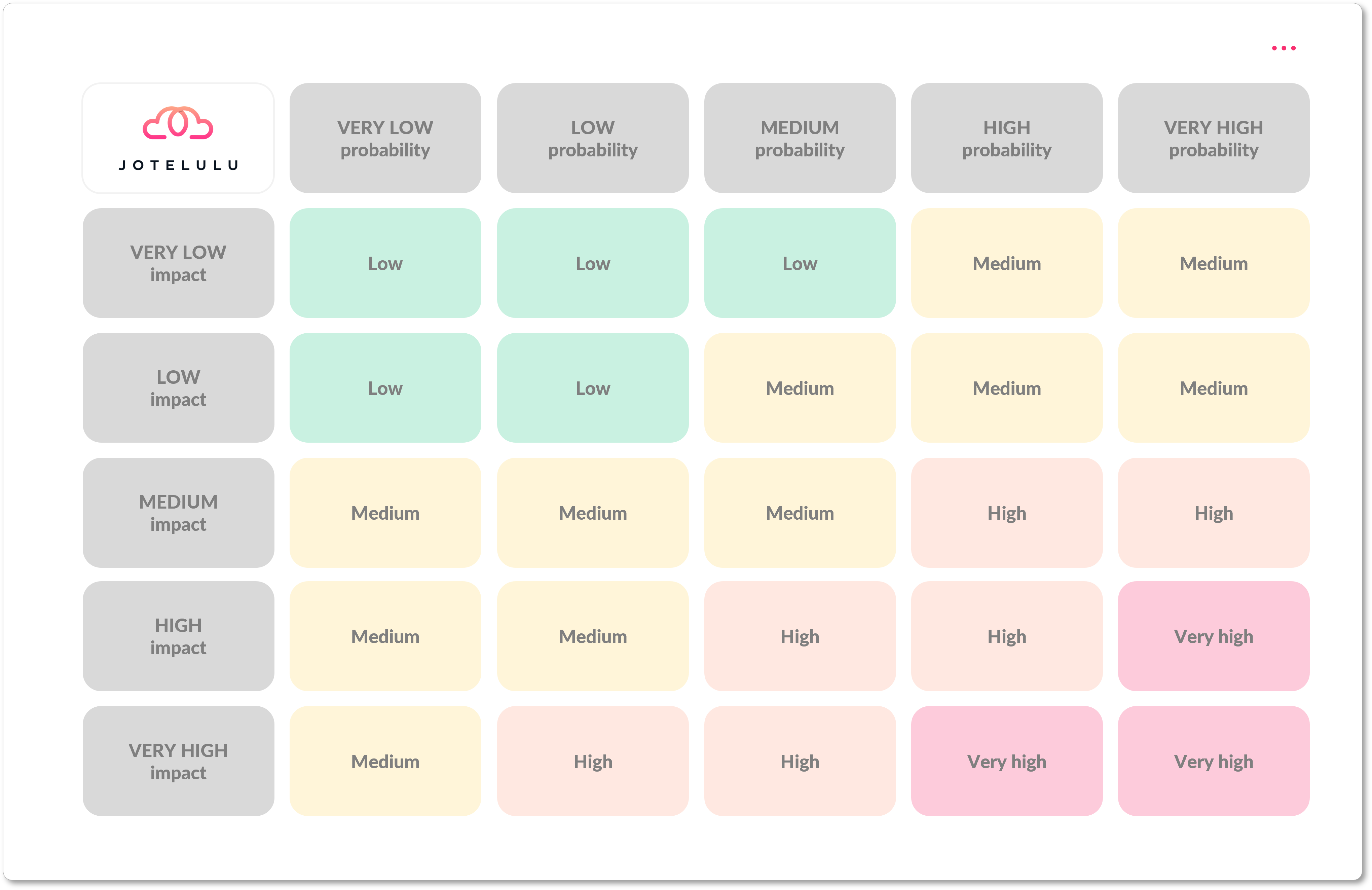
Once you have carried out this exercise, you can then create a risk matrix, like the one shown below, which helps to visually show the potential risks using a colour map.
Step 7: Implement mitigating actions
Now that you’ve carried out a thorough analysis of the potential threats, it’s time to identify what potential actions you could implement to reduce or eliminate the associated risks. Obviously, you should start with the most critical items or those that can be easily eliminated.
There are essential four basic approaches to mitigating threats:
- Transfer the risk: This means the risk is taken care of by a third party, such as an insurer or a sub-contractor.
- Eliminate the risk: This is normally done by removing the machine or service involved. Otherwise, it’s quite complicated.
- Accept the risk: This is a common approach when the cost of reducing or eliminating the risk is far greater than the potential impact if the threat occurs. However, this DOES NOT APPLY if the threat poses a risk to human life.
- Mitigate the risk: This approach is chosen when a risk cannot be completely eliminated but it can be reduced or mitigated. An example of this are server clusters.
Step 8: Implement control measures
Once you’ve come up with your mitigating actions and reduced all the potential risks as much as possible, it’s time to implement some control measures in order to keep risks at acceptable levels.
To do this, you should establish an investment strategy to ensure that policies and procedures are up to date and new technology is adopted where possible. You should also ensure that technical staff are fully trained and that all employees are fully aware of the importance of IT security and the policies adopted by the company.
Step 9: Continuous Improvement
The final step in the process is to make sure that you don’t rest on your laurels. You may have done a lot of work, but it will all be for nothing if you don’t review your assessments and update them when new threats or risks emerge.
There’s no point in establishing a risk management policy if it’s not up to date. Threats are constantly evolving, and you will need to make an effort to keep up with them.
This means carrying out regular risk assessments, keeping up to date with the latest viruses, bugs or vulnerabilities and making sure that everything is well documented.
Conclusion
In this article, we have taken a closer look at risk and threat assessment for SMEs and we have set out a 9-step method to help you get started. While this method might be a bit of a deviation from the traditional 6-step method, we think it makes the different tasks easier to understand and allows us to put a special emphasis on continuous improvement.
We hope that this article helps you to identify the threats to your business and mitigate the risks accordingly. That way, you can be sure that you have protected your business for the long term and are well-prepared should disaster strike.
If you would like to learn more about business continuity planning, check out some of these articles:
- Why is Disaster Recovery Such a Headache?
- Disaster Recovery: What Is It and Why Do We Need It?
- Disaster Recovery: What are RPO, RTO, WRT and MTD?
Thanks for reading!