In this tutorial, you will learn how to configure the ports for your Remote Desktop service, as well as other security recommendations that will help keep your business’ infrastructure protected against the majority of attacks that you may face.
The Remote Desktop Protocol (RDP) is a protocol developed by Microsoft to enable a connection between a client device and a remote server running applications, allowing the user to interact with the server using their own mouse and keyboard as though the application was installed on the client device.
One of the most common security mistakes when setting up a Remote Desktop is using the default ports as these are some of the first ports to be scanned by hackers planning an attack.
The default port for an RDP connection is 3389/TCP, and for a normal Remote Desktop installation, you would need to change this to a different point. In principle, this shouldn’t be necessary for those using the Jotelulu Remote Desktop service because it already uses HTML5 through port 443/TCP, which is an encrypted port that allows the use of any modern web browser, whether on Windows, iOS or GNU/Linux.
Nonetheless, we are still going to use this opportunity to explain how to configure your Remote Desktop ports and ports on other Jotelulu servers so that you are able to make the necessary changes so that your applications always run correctly.
How to configure remote desktop ports on Jotelulu
Before you get started:
To successfully complete this tutorial and change your Remote Desktop settings, you will need:
- To be registered on the Jotelulu platform and have logged in.
- To have registered an organisation with users in a way that you can link users to the remote desktop environment and its applications. If you would like to find out more about how to register users, we recommend reading the tutorial entitled How to Register Users on Jotelulu.
Part 1 – Configuring your Remote Desktop ports
You can either change your port settings when initially setting up your Remote Desktop or at any time later on.
If your Remote Desktop service has already been deployed, you will need to access the Remote Desktop page on the platform. If you wish to change your port settings whilst deploying the service, you can skip this part of the tutorial.
On the Jotelulu platform, click on the Remote Desktop card to open the Remote Desktop page (1).
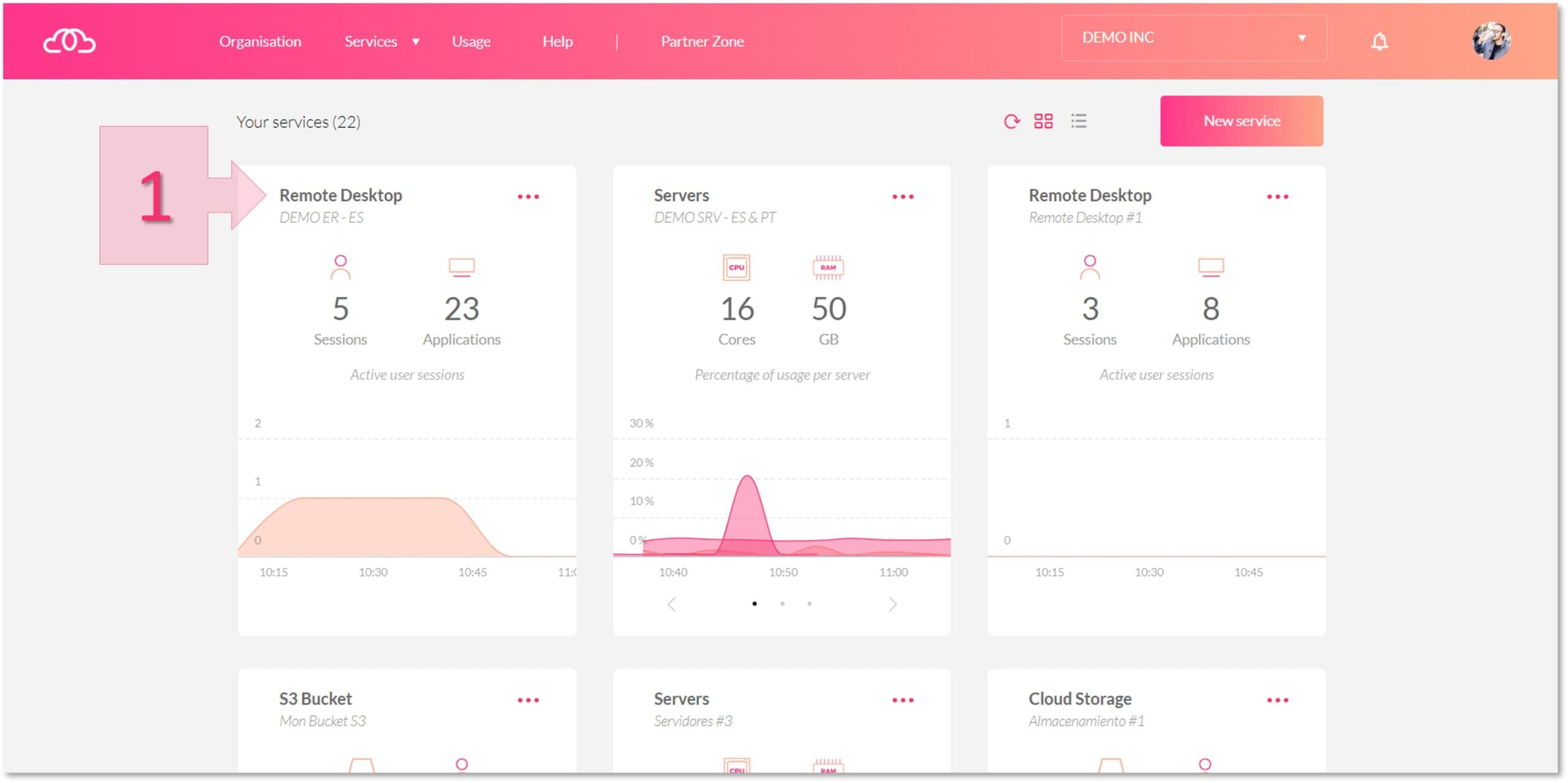
Once you are on the Remote Desktop page, click on Server in the left-hand menu (2). Scroll down the page and you will see “Firewall – Inbound Rules”. Here, you have the option to see existing rules or create new ones.
Click on “Create new inbound rule” (3).
Next, you will need to fill in a number of fields. Select the network (4) that you are working on and then, under “IP or Network” (5), select “Any IP Address”. This will allow connections from any point. Alternatively, you can manually enter the IP address or range for which you wish to allow access.
Next, in the “Firewall” section, you will need to select the port that you wish to open. First, under “Protocol” (6) select TCP or UDP depending on the communication protocol you wish to use. Next, enter the Public IP address (7) you are using, and lastly, enter the “Public Port” (8) that you wish to connect through.
In the “Server” section at the bottom of the page, select the “Private IP Address” (9) and enter the “Private Port” (10). Once you have done all of this, click on “Continue” (11) to save your changes.
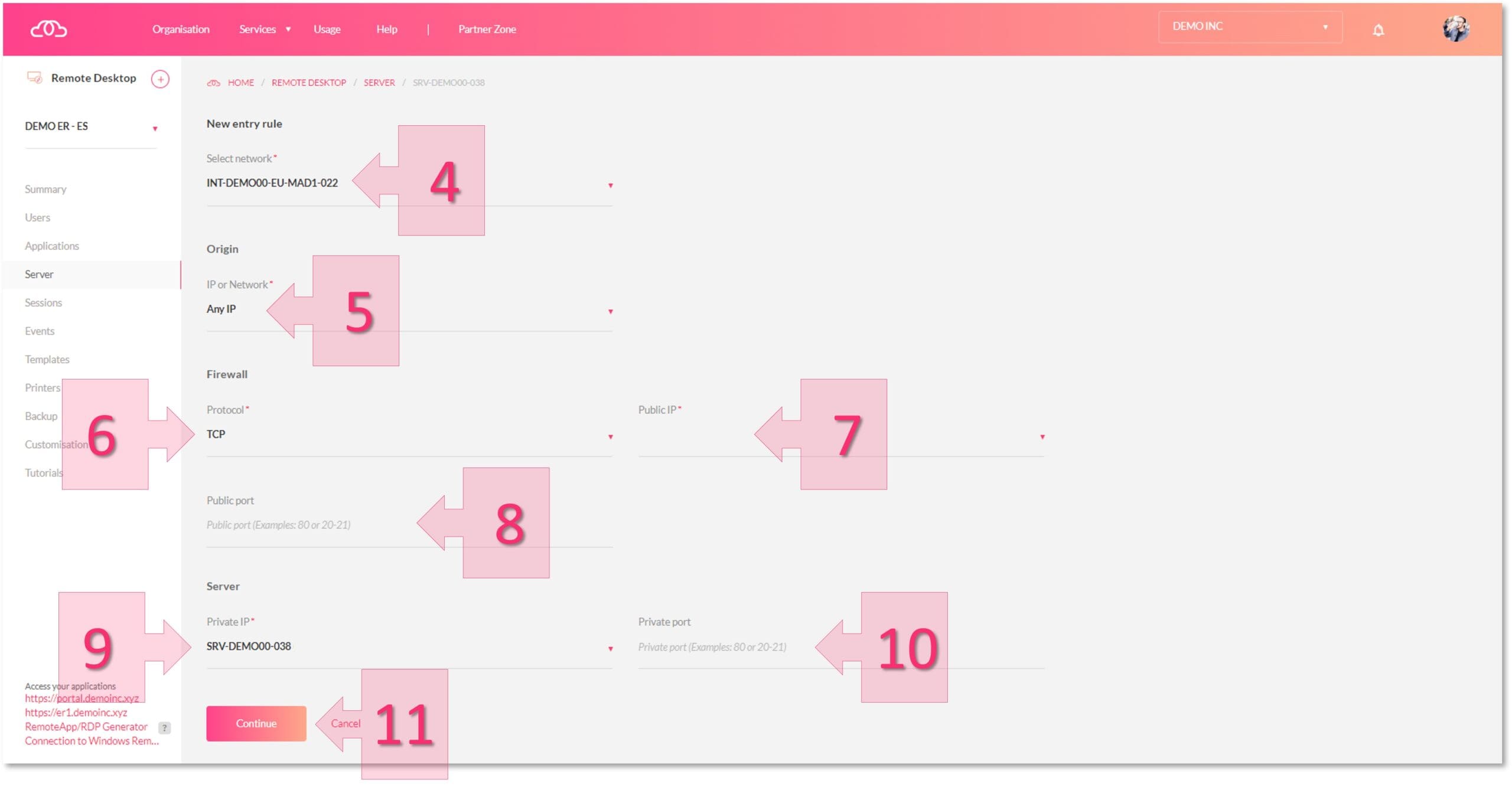
You have now created a new inbound rule.
Part 2 – Other security recommendations for Remote Desktop
Another good way to keep your infrastructure secure is the use of a VPN connection. In fact, this is something that we recommend at Jotelulu, and we go into more depth on this subject in the tutorials titled How to Configure a Remote Access VPN Connection and How to Connect to the Remote Desktop Using a Site-to-Site VPN (jotelulu.com).
As a general policy, we also recommend implementing some form of additional perimeter security. Aside from classic Firewalls and antivirus protection, which we always recommend installing on all devices and servers, we also recommend Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS).
IDSs are applications that monitor the network and connected devices to identify unauthorised access attempts. When such an attempt is detected, depending on the system settings, the event will be recorded in a log and an alert will be sent (by e-mail, for example) so that the user or administrator can review the issue and take the necessary action.
IPSs, on the other hand, are like a more advanced form of IDS, although the truth is they are more like a firewall. Unlike IDSs, they don’t just monitor network traffic and send alerts. They are also capable of making decisions and taking action themselves, following a set of predetermined rules, which significantly increases network security. However, these systems require much more effort to set up.
These systems are good forms of protection against various types of attacks, such as brute-force attacks that attempt to exploit vulnerabilities or security breaches. However, we should also remember the importance of keeping your company’s infrastructure up to date. This means all components, including clients, servers and Remote Desktop servers. Ideally, you should have a bank of machines to try updates on first so that you can detect any potential issues before updating the rest of your infrastructure.
Conclusions and next steps:
Configuring and securing a remote desktop environment involves deploying two subscriptions (remote desktop and servers), and the ports used could be important when setting up other tools such as firewalls, IDSs or IPS.
It is possible to manage everything related to users, permissions, applications and licences from the Remote Desktop section on the platform.
In this tutorial, you have learnt how to change the ports for your Remote Desktop service as well as learning about other security measures that can protect your infrastructure.
If you found this tutorial useful and would like to find out more about related topics, you might wish to read the following tutorials:
- How to Link a Remote Desktop User to a Domain User
- How to Configure a Remote Access VPN Connection
- How to Connect to the Remote Desktop Using a Site-to-Site VPN
We hope that you found this information useful.
And remember that if you have any other questions, you can get in touch with our help service.
Thank you for choosing Jotelulu!





