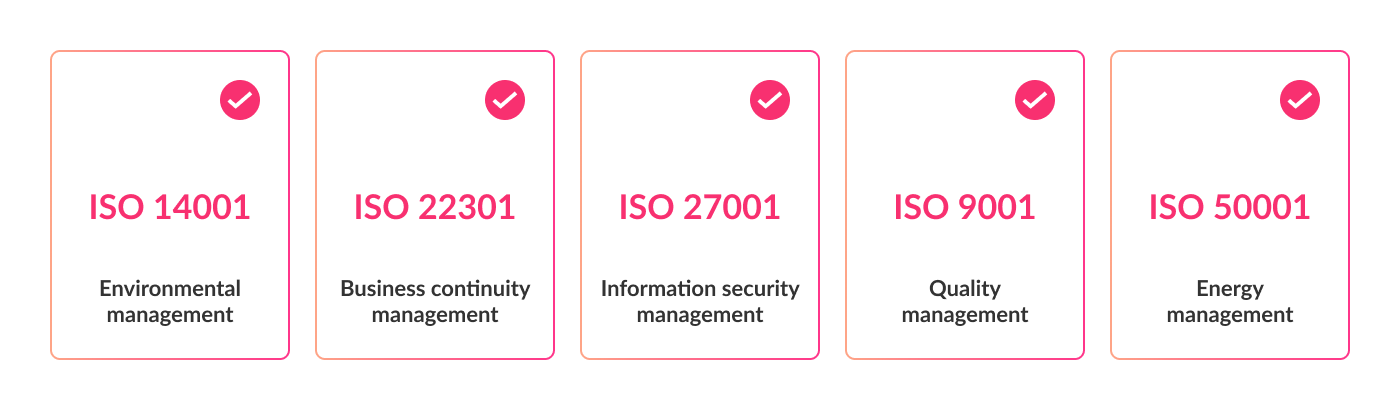
Our platform and data are hosted at highly efficient neutral data centres that boast the very best connectivity and security measures.
We only use cutting-edge centres in Europe and the Americas that are internationally recognised as leaders in technology and reliability.
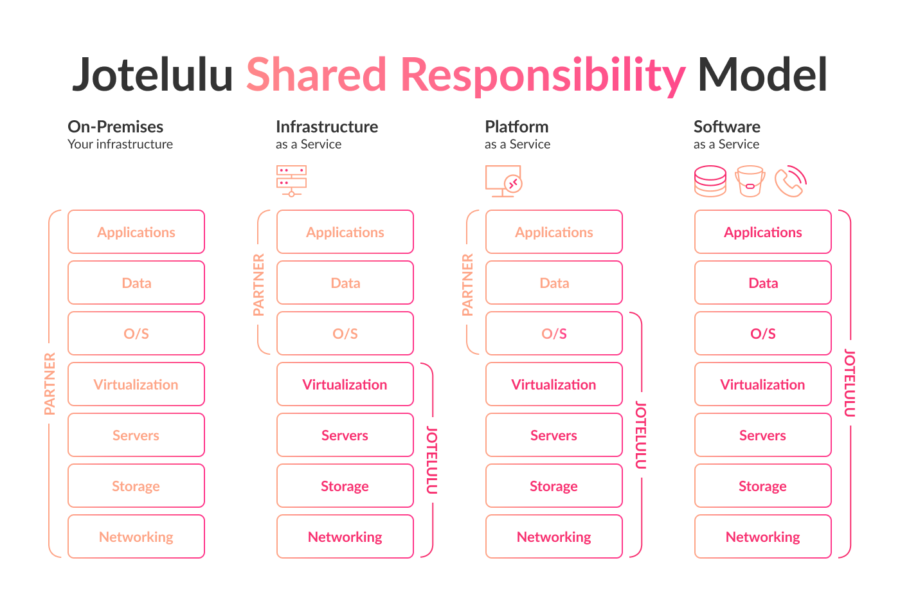
At JOTELULU, our infrastructure is designed to include multiple layers of security to ensure reliability and proactively protect our cloud services. From system redundancy to advanced protection measures, our infrastructure guarantees business continuity for all our partners and customers.
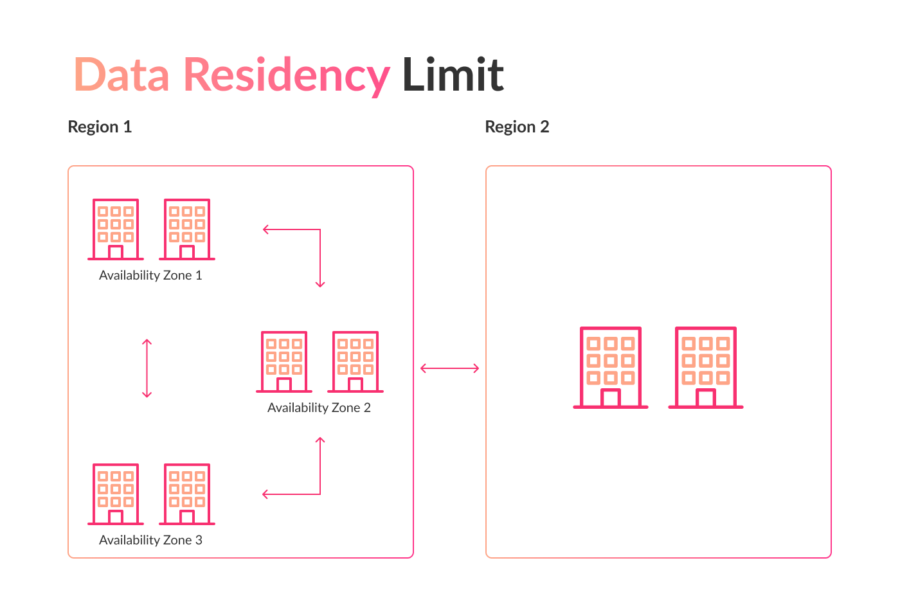
We use efficient, high-security data centres strategically distributed across multiple regions to ensure an uninterrupted user experience. This global infrastructure allows our partners to bring their services closer to their customers while maintaining data residency and regulatory compliance, regardless of geographic location.
Our services use availability zones, which are physically separate locations within each region. These zones have independent power, cooling and network connections to ensure high availability and low-latency replication for critical applications. This design provides an unbeatable resilience against system failures and allows rapid and secure disaster recovery.
With JOTELULU, your cloud infrastructure is built on solid foundations that provide security, flexibility and world-class performance so you can adapt to your customers’ needs, wherever they are in the world.
Geographically distributed data centres allow our partners to reduce network latency and enable backups and failover with geographic redundancy.
When choosing the location of our data centres, we prioritise proximity to our partners to ensure minimum latency and optimum performance. The sites for our data centres are strategically chosen to mitigate risks such as flooding, extreme weather and seismic activity. Each availability zone is independent and physically isolated to guarantee resilience and protection against adverse situations.
Our data centres guarantee 99.999% availability for our customers’ services thanks to our agreements with the most recognised and reliable data centres in the world, such as Digital Realty and Data4. These partners operate latest-generation facilities designed to provide maximum security, redundancy and uninterrupted availability, which, in turn, enables JOTELULU to deliver extremely reliable services.
Our business partners’ investment in these global operations guarantees that our infrastructure is robust and well-managed, with constant supervision, advanced network and sustainable practices that enhance energy performance. These data centres operate 24 hours a day, 7 days a week, 365 days a year, ensuring that our customers’ critical needs are always covered.
Our infrastructure boasts multiple levels of redundancy and guarantee service continuity at all times. To minimise any interruption, we have redundant systems to protect critical facilities and ensure that data remains secure and accessible. Local redundancy at the disc level protects data within each region, while geographic redundancy extends this protection across various locations, improving data availability and security.
To ensure the reliability of our network connections, we use fibre optic links and redundant hardware to protect special components against potential failures. Furthermore, we use geographic replication to make sure that we always have a secure copy of data in alternative locations, maximising data durability and availability.
Data is synchronised regularly between different locations, while restore tests are performed regularly to validate the integrity of our backups.
At JOTELULU, we continuously monitor the use of our services to ensure that we meet our commitments in terms of availability and the requirements of our users.
Our capacity planning model regularly evaluates system demand and the use of our infrastructure, and we carry out monthly reviews to anticipate future needs. This approach means that we can proactively adjust resources, taking into considering key factors such as data processing, telecommunications and the secure storage of audit logs.
The data centres supporting JOTELULU’S infrastructure are powered by 24/7 uninterruptible power supplies (UPS) and emergency power systems, which include local generators to provide backup power. The UPS and generators are regularly tested and maintained to ensure that they are in full working order. In addition, we have contractual agreements with local suppliers for rapid emergency fuel deliveries where necessary. Our data centres also have dedicated operations centres that constantly monitor the power system, including critical electrical components.
Electrical redundancy is a fundamental way of guaranteeing availability, through use of multiple power sources and backup systems, such as generators and UPS. In the event of a power cut, the UPS system activates immediately to maintain a supply of power until the generators come online. The generators then ensure a continuous supply of power during prolonged power cuts, maintenance tasks or emergency situations, with fuel reserves available in the event of a natural disaster.
At JOTELULU, we are fully aware of the amount of electricity consumed by our data centres, and we are committed to sustainability through the use of renewable energy. This approach allows us to considerably reduce our environmental footprint by minimising the CO₂ emissions associated with our operations, further contributing to a cleaner and more responsible future.
Our Operations team implements energy efficiency strategies that cover all aspects from the design of each facility to 24/7 continuous monitoring. We monitor electricity consumption, cooling systems and shared infrastructure to optimise efficiency and guarantee that every aspect of our operations is as environmentally friendly as possible.
In addition, we take active steps to compensate the CO₂ emissions that we generate, whether produced by electrical generators or by the travel required for daily operations.
As part of our overall commitment, we also work with other companies in the sector as part of initiatives like the European Climate Pact. This EU-led initiative sets ambitious targets to decarbonise digital infrastructure and achieve climate neutrality by 2030. In line with these objectives, we prioritise the use of renewable energy to contribute towards the sustainability of the sector.
At JOTELULU, we guarantee the safety of our facilities using advanced fire detection and suppression systems connected to isolated power sources to ensure they are operational at all times. Strategically located water sensors monitor potential water ingress or leaks and notify staff immediately to prevent damage.
Our facilities are also fitted with advanced smoke detectors and double interlock sprinkler systems to protect critical equipment. Daily inspections and continuous monitoring ensure that all security requirements are rigorously adhered to.
Our leak detection systems are equipped with alarms for rapid response, ensuring that both fires and floods are managed efficiently to protect our infrastructure and customer data.
All access events and requests are logged and preserved as part of an electronic audit, enabling close control and the detection of anomalies to prevent unauthorised access. Our CCTV system monitors critical areas, such as entrances, cages, cabinets and perimeter areas, and recordings are kept for at least 90 days, unless otherwise required by law.
Physical access is continuously monitored by a security control team, supported by a CCTV system linked to the alarm system. Only authorised personnel can access our facilities and any equipment that enters or leaves the site is rigorously controlled. Any security events are logged in detail and analysed in order to devise corrective actions to strengthen security.
With CCTV and a 24/7 alarm system, JOTELULU guarantees maximum protection of its facilities and resources.